"ls" on Mac and extended file attributes
Yesterday while I was working in the terminal I noticed something unusual about the results of “ls -al” command:
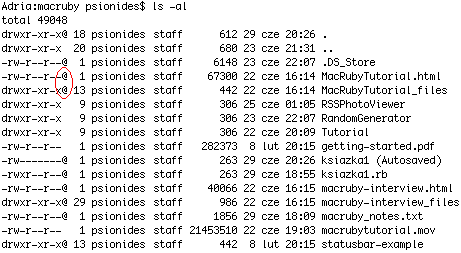
What are those symbols? I googled for “mac ls at sign”, but most of the results told me that “@” means “symbolic link”. Well, all those files can’t be symbolic links, I’m pretty sure of that. So what are they?
I found the answer in a mail on Apple mailing list. It seems that the @ symbol means that the file has something called “extended attributes”. The attributes are a kind of metadata about the file stored in a special place in the HFS filesystem, not visible during normal browsing. As I learned from a Wikipedia page, most of popular filesystems support such metadata – although I’ve never heard such thing existed in Windows or Linux… The mail also said that apart from “@”, files can have “+” symbol, which means that they have non-standard permissions set using some kind of ACLs.
The mail explained that you can print that metadata by adding a –@ option to ls. I did that, and learned that some of the files had an attribute “com.apple.TextEncoding”, and some others – “com.apple.quarantine”. It’s easy to guess what TextEncoding is for, but quarantine? WTF?
Again, a quick Google search solved the mystery – the quarantine tag is what causes those messages “xxx is an application which was downloaded from the Internet. Are you sure you want to open it?” that I get when I run an application for the first time. Every file (not only applications, it seems) that is downloaded from the Internet is marked with this quarantine metadata tag. When the user confirms that he wants to open the file, the tag is removed and the popup doesn’t appear again.
There is a command line utility for accessing and managing that metadata, named xattr. It can print file’s metadata attributes and their values, modify attributes and remove them, like this:
$ xattr macruby-interview.html
com.apple.quarantine
$ xattr -l macruby-interview.html
com.apple.quarantine: 0000;485e5e65;Firefox;|org.mozilla.firefox
$ xattr -w pl.psionides foo macruby-interview.html
$ xattr macruby-interview.html
com.apple.quarantine
pl.psionides
$ xattr -l macruby-interview.html
com.apple.quarantine: 0000;485e5e65;Firefox;|org.mozilla.firefox
pl.psionides: foo
$ xattr -d pl.psionides macruby-interview.html
$ xattr -d com.apple.quarantine macruby-interview.html
$ xattr macruby-interview.html
$ ls -l macruby-interview.html
-rw-r--r-- 1 psionides staff 40066 22 cze 16:15 macruby-interview.html
As you can see, the metadata store not only the information that a file was downloaded from the Internet, but also how it was downloaded (using Firefox), and I think also when it was downloaded (the hex value). The -d option can be useful if MacOSX for some reason forgets to remove the quarantine attribute, which – as I’ve read – can happen sometimes.
10 comments:
Mitch
Nice synopsis. I was looking for just this information.
Daniel
This was exactly what I was looking for. I've been hunting down this info for hours now....ehg.
LeAnne
Yes! Thanks so much - I've also been looking for this for a couple of hours!
MP
Me too! Thanks a lot.
kangfucius
Excellent summary. Thank you
hzlzh
Thx, got it and remove it by line below;
>xattr -l 1.plist
com.macromates.selectionRange: 39:32
>xattr -d com.macromates.selectionRange 1.plist
>ls -l
Raghu
That was really help Jakub. It enlightened me.
Tom vC
Thanks, helpful!
matt
Great summary. Thanks a bunch.
Jefferson Gouveia
Thanks very much!